Kerberos
Kerberos Verificatiesysteem ontwikkeld door Massachusetts Institute of Technology MIT. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet.

Kerberos Explained Security Companies Band Patches Microsoft
A free implementation of this protocol is available from the Massachusetts Institute of Technology.

Kerberos. Deploy your own video surveillance system in a few minutes anywhere you want using Raspberry Pi Docker or Balena Cloud. MA-VRIJ 9u - 12u30 13u - 19u ZAT 9u - 12u ZO Wachtdienst. Kerberos is available in many commercial products as well.
Microsofts Kerberos implementation in Active Directory has been targeted over the past couple of years by security researchers and attackers alike. Genoemd naar de driekoppige hond die volgens de Griekse mythologie de ingang van Hades bewaakte. οι πυρκαγιές βρίσκονται ακόμη σε εξέλιξη έγιναν στάχτη πάνω από 270000.
Transparent video surveillance for everybody everywhere. The issues are primarily related to the legacy support in Kerberos when Active Directory was released in the year 2000 with Windows Server 2000. Kerberos protokół uwierzytelniania i autoryzacji w sieci komputerowej z zastosowaniem centrum dystrybucji kluczy zaprojektowany w Massachusetts Institute of Technology MIT.
Kerberos-verificatie en het oplossen van problemen met overdracht. ευρωπαϊκής πλατφόρμας Forest Fire Information System FFIS καθόσον ότι. 0x10 KDC has no support for PADATA type pre-authentication data.
KERBEROS Leuven Tiensesteenweg 170 3001 Heverlee Leuven 016252717 016260389 infokerberosbe. Our Kerberos RTL-SDR driver branch contains code for slightly modified Osmocom RTL-SDR drivers that enable GPIO disable dithering and disables zerocopy buffers which seems to cause trouble on some ARM devices. Sie ist in RFC 4120 definiert und nutzt ASN1 zur Codierung.
Kerberos Pre-Authentication types. For more information see Table 5. Kerberos runs as a third-party trusted server.
Kerberos ist ein verteilter Authentifizierungsdienst Netzwerkprotokoll für offene und unsichere Computernetze wie zum Beispiel das Internet der von Steve Miller und Clifford Neuman basierend auf dem Needham-Schroeder-Protokoll zur Authentifizierung 1978 entwickelt wurde. Als u deze kolom aan uw behoeften wilt aanpassen nodigen we u uit uw ideeën over onderwerpen in te dienen die interessant zijn voor u en problemen die u in toekomstige behandeld wilt zien worden in Knowledge Base-artikelen en in kolommen voor spraak-ondersteuning. Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials.
It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. Hes a big 3 headed dog with a snake for a tail and a really bad temper. According to myth Kerberos you might know him as Cerberus guards the Gates to the Underworld.
Kerberos is a network authentication protocol. Powstało też wiele interfejsów programistycznych pozwalających wbudowywać mechanizmy bezpieczeństwa dostarczane przez serwer Kerberos do aplikacjiJednym z nich jest interfejs w języku Java nazwany General. Consultaties enkel op afspraakAfspraak.
Met Kerberos kan vertrouwelijke informatie worden verzonden via een openbaar netwerkzoals het Internet. The core product backbone of the entire Kerberosio ecosystem completely free and open source. Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users.
This legacy support is enabled when using Kerberos RC4 encryption. In the modern world MIT Computer Scientists used the name and visual of Kerberos for their computer network authentication protocol. Kerberos Authentication Explained.
In Kerberos Authentication server and database is used for client authentication. Value is not 138 when Kerberos Armoring is enabled for all Kerberos communications in the organization. Een veilig gevoel bij elk doel.
Een monsterlijke hond met drie koppen in sommige verhalen zelfs 50 of 100 en soms met een slangenstaart of draak als staart en ontelbare slangenkoppen op zijn rugHij en Orthros de tweekoppige hond van de reus Geryon werden geschapen door Echidna en Typhon. Die zurzeit aktuelle Version ist Kerberos 5. Sudo apt-get install libusb-10-0-dev git cmake git clone https.
Kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services. Cerberus is een figuur uit de Griekse mythologie. It uses secret-key cryptography and a trusted third party for authenticating client.

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

Cluster Dedicated Kdc Kdc On Master Node Emr Big Data Master

Cerberus Or Kerberos In Greek And Roman Mythology Is A Multi Headed Usually Three Headed Dog Or Hel Greek And Roman Mythology Greek Mythology Greek Myths

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access

What Is Kerberos And How It Works Social Media Infographic Computer Network Infographic
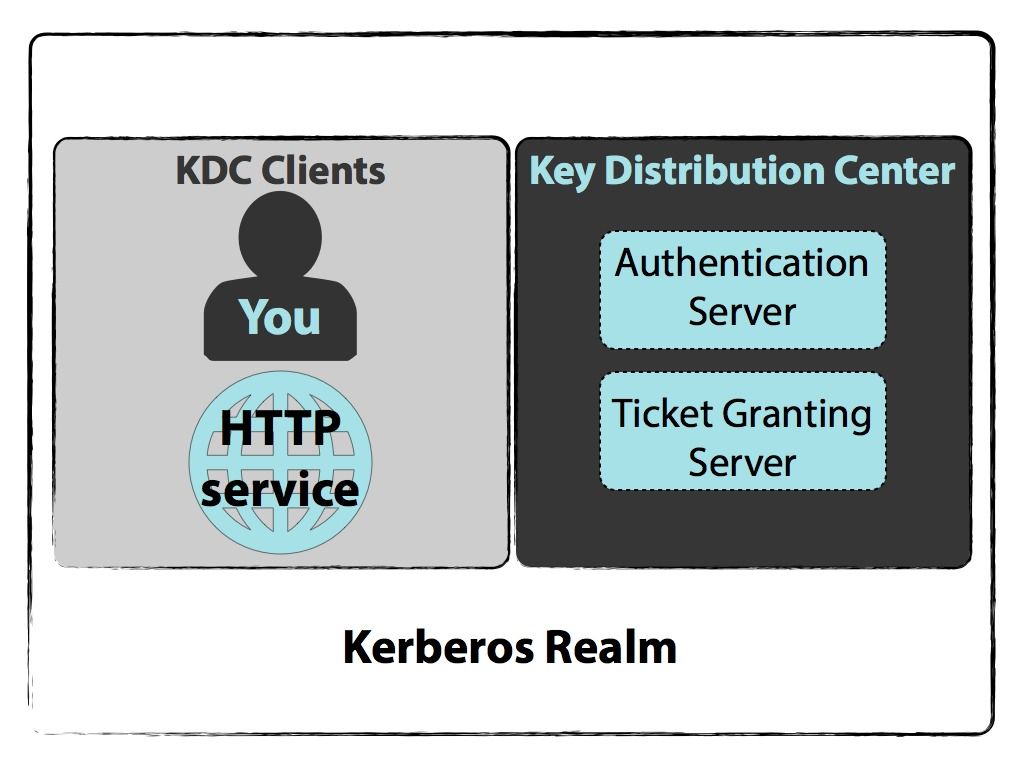
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

Kerberos Saga Tetsuro Kai In Genx Core 18 Off 16 174 Jpy Armor Concept Sci Fi Concept Art Futuristic Armour

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base

Cracking Kerberos Tgs Tickets Using Kerberoast Exploiting Kerberos To Compromise The Active Directory Domain Active Directory Innovation Technology Domain

Kerberos Architecture Computer Help Windows Server Microsoft


Kerberos Architecture Computer Help Windows Server Microsoft

Selecthiveql Nifi Connection Hives

Kerberos Art From Soul Sacrifice Art Artwork Gaming Videogames Gamer Gameart Conceptart Illustrat Fantasy Creatures Mythical Creatures Creature Concept


Kerberos Saga Armor Concept Dieselpunk Retro Futuristic

Apache Storm Due To Its Comprehensive Feature Helps Enterprises To Process Data Faster Solving Complex Data Problems In Storm Online Learning Machine Learning

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux

Kerberos Hosting Intro