Kerberos Authentication
This API might receive a series of flags to indicate whether the browser allows the delegatable ticket the user has received. The benefits gained by using Kerberos for domain-based authentication are.

Authentication Fails When A Windows Client Accesses A Cifs Share Because The Kerberos Authentication Ticket Is Cached In 2021 Windows Client Fails Clients
The API in question is InitializeSecurityContext.

Kerberos authentication. Stop account takeovers by asking users or customers to simply take a selfie. Using Kerberos authentication within a domain or in a forest allows the user or service access. It is designed for client-server applications and requires mutual verification.
Kerberos is a network authentication protocol. Kerberos a network authentication protocol included in the Microsoft Windows operating systems can be used in conjunction with Security Support Provider Interface SSPI to provide pass-through authentication with secret key cryptography and data integrity. Kerberos at its simplest is an authentication protocol for clientserver applications.
Advertentie Authenticate and reverify users or customers with Veriffs facial biometric technology. This request consists of the PC Client TGT and an authenticator. Kerberos is available in many commercial products as well.
Kerberos is the default protocol used when logging into a Windows machine that is part of a domain. Kerberos authentication protects user credentials from hackers. These are the steps in Kerberos Authentication.
Services that run on Windows operating systems can impersonate a client computer when. Microsoft introduced their version of Kerberos in Windows2000. The protocol was initially developed by MIT in the 1980s and was named after the mythical three-headed dog who guarded the underworld Cerberus.
It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. Lets see how all of this works. In order to setup Kerberos for the site make sure Negotiate is at the top of the list in providers section that you can see when you select windows authentication.
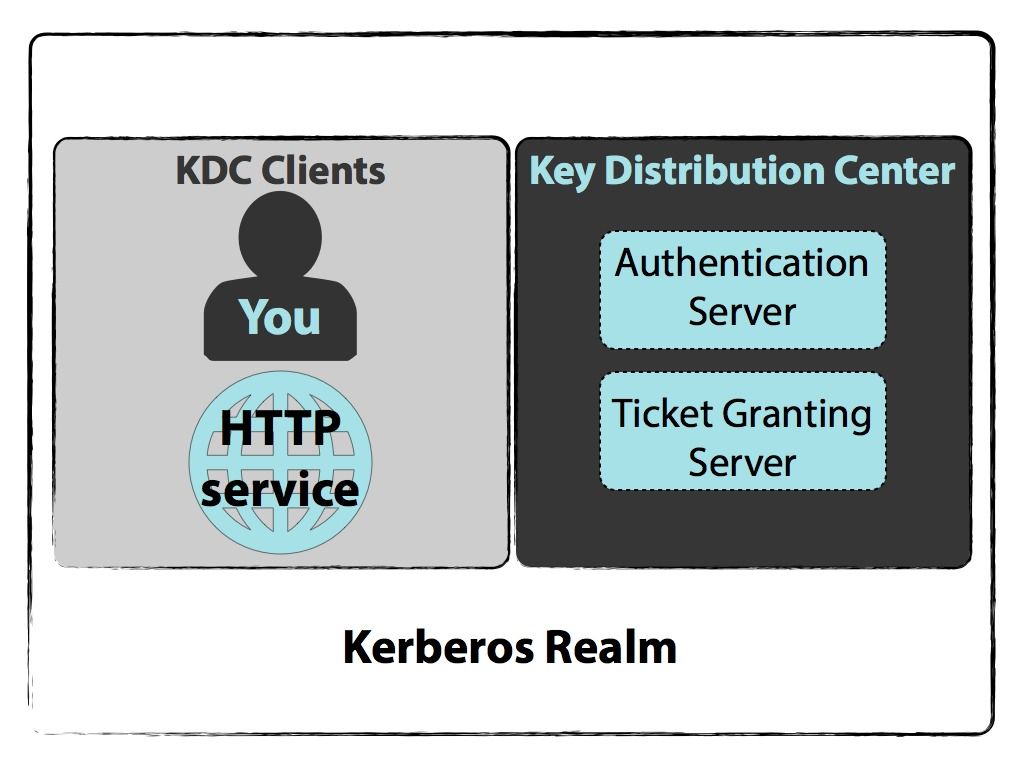
In Kerberos Authentication server and database is used for client authentication. Clients authenticate with a Key Distribution Center and get temporary keys to access locations on the network. This allows for strong and secure authentication without transmitting passwords.
A Ticket-Granting Ticket TGT request is sent to a Kerberos KDC. Active Directory performs the functions of the KDC. It might also use NTLM which is also a provider in windows authentication.
The Kerberos KDC returns a TGT and a session key to the PC Client. Stop account takeovers by asking users or customers to simply take a selfie. PC Client logs on the domain.
Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. A ticket request for the application server is sent to the Kerberos KDC. Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC.
Kerberos is an authentication protocol. Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux. This protocol keeps passwords away from insecure networks at all times even during user verification.
Active Directory AD is a component running on the DC that. Advertentie Authenticate and reverify users or customers with Veriffs facial biometric technology. The two servers combined make up a KDC.
A free implementation of this protocol is available from the Massachusetts Institute of Technology. Kerberos also requires an Authentication Server AS to verify clients. Basically Kerberos is a network authentication protocol that works by using secret key cryptography.
The user database in this case is on the Domain Controller DC. When an attempt is made to authenticate to a website using Kerberos based authentication the browser calls a Windows API to set up the authentication context. The following figure shows the sequence of events required for a client to gain access to a service using Kerberos authentication.
Each user and service on the network is a principal. Read on to learn what Kerberos authentication is and how it protects both end-users and systems. Its designed to provide secure authentication over an insecure network.

Register A Spn For Sql Server Authentication With Kerberos Sql Server Microsoft Sql Server Sql

Part3 Troubleshooting Kerberos Authentication And Things To Check When It Fails Fails Microsoft Dynamics Recruitment

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base

Authentication Fails When A Windows Client Accesses A Cifs Share Because The Kerberos Authentication Ticket Is Cached In 2021 Windows Client Fails Clients

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux

Optimizing Ntlm Authentication Flow In Multi Domain Environments Cyber Security Optimization Computer Server

Kerberos Architecture Computer Help Windows Server Microsoft

Sap Hana Authentication Methods For Verification Of User Identity Username Password Kerberos Saml Sap Logon Tickets And Assertion Sap Hana Markup Language

Flink Configuring Kerberos Authentication Huawei Enterprise Support Community Unified Communications Public Security Ip Telephony

Pin On Storage

Using Sql Service Broker For Asynchronous External Script R Python Execution In Oltp Systems Sql Relational Database Management System Sql Server

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access

Mongodb Authentication With Kerberos Regular Expression Data Storage Reading

Cracking Kerberos Tgs Tickets Using Kerberoast Exploiting Kerberos To Compromise The Active Directory Domain Active Directory Innovation Technology Domain
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

Kerberos Authentication Architecture Ile Ilgili Gorsel Sonucu Cryptography Architecture Kas

Kerberos Architecture Computer Help Windows Server Microsoft

Configuring Kerberos Authentication In Different Browsers Browser Internet Options Web Server

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide